7 Cybersecurity Practices for Legal Firms
By: Karl Bickmore, COO, Snap Tech IT
Handling sensitive data that attracts hackers and malicious insiders is part of everyday life in a law firm. The majority of security breaches lead to some form of reputational losses, remediation costs, and penalties. That’s why there are 7 cybersecurity best practices at law firms should have in place.
Complying with all necessary regulatory requirements and implementing cybersecurity protection measures that fit your organization is an enormous challenge. When you think about protecting your confidential data from a cyber-attack, it’s a good idea to put it in perspective: It’s not a matter of “if” an attack will happen, it’s a matter of “when” and if your organization will be prepared to respond and recover from it. We’ll explore the reasons for and types of security breaches in legal organizations and show you how to prevent them by implementing best practices for complying with IT requirements.
Under Attack: The Facts on Cybersecurity Threats in the Legal Industry
The number of cybersecurity breaches in the legal industry has been growing year over year. According to the American Bar Association’s Legal Technology Survey Report, 26% of law firms report they’ve suffered from a breach at some point in their history. Another 19% say they don’t know whether their organization has been breached. Really?
This is frightening when you think about the consequences of compromised data and the frequency in which it is happening. Not to mention the negative impact these breaches have on the firm’s bottom-line:
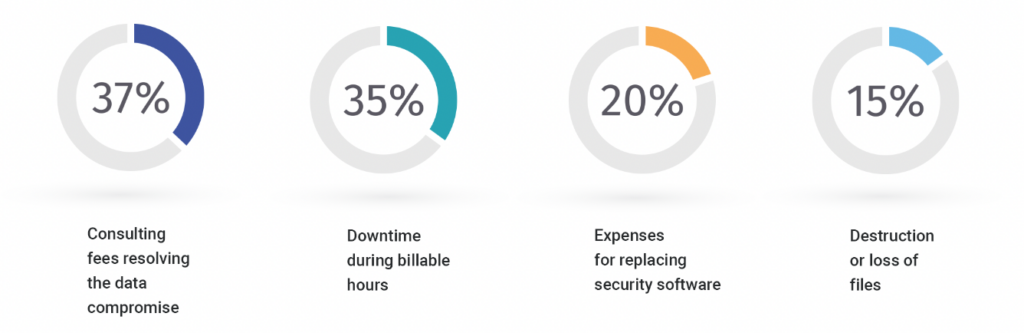
One of the most common reasons for data breaches is an insider attack. A recent study shows that 96% of IT leaders in the legal industry believe an insider breach to be a significant risk for their organization.
Insider threats come from within an organization in the form of employees and third-party contractors that have access to the environment. Employees or sub-contractors may intentionally or unintentionally leak sensitive information or provide hackers with access to it. Insider threats are as dangerous as outside hacker attacks because insiders have good knowledge of the law firm’s cybersecurity measures and the sensitive data a firm manages.
Let’s take a look at several key motivations for malicious insider activity:
- Hacktivism — Leaking sensitive data for political and social reasons
- Sabotage — Doing damage as a disgruntled employee
- Personal gain — Stealing sensitive data for insider trading or opening a new law firm
- Espionage — Breaching data on behalf of market competitors or other states
Following Data Compliance Requirements
Depending on your firm’s specialization, your law firm may work with various types of sensitive client information including personal, financial, and healthcare data. Each of these types of data is protected by security standards, laws, and regulations. There are also specific recommendations from key cybersecurity and legal organizations that law firms should follow.
Failure to comply with these cybersecurity compliance requirements may prove fatal for a law firm. Not only could it lead to legal challenges and investigations but can also damage the company’s reputation and trigger client loss. Here’s a snapshot of key regulations, laws, and standards that apply to law firms.
- ABA Model Rules of Professional Conduct
- NIST Special Publication 800-53
- Regional Laws
- Industry acts, standards & regulations
- GDPR
ABA Model Rules of Professional Conduct
Law firms based in the U.S. must follow the Model Rules of Professional Conduct developed by the American Bar Association — the biggest professional organization for lawyers in the U.S. The American Bar Association develops rules that ensure legal services are ethical, efficient, and safe. Its Formal Opinions 477R and 483 describe methods required to monitor for data breaches, implement security measures to counteract attacks, notify clients of a breach, and remediate the damage of a breach. Both Formal Opinions compel lawyers to “make reasonable efforts to prevent the inadvertent or unauthorized disclosure of, or unauthorized access to, information relating to the representation of a client.”
NIST Special Publication 800-53
The National Institute of Standards and Technology (NIST) established and maintains Special Publication 800-53, a complete set of cybersecurity practices and regulations for U.S. federal agencies. Complying with these regulations is beneficial for all organizations because it verifies the effectiveness of implemented protection measures and provides a competitive data security advantage.
TIP: When it comes to implementing cybersecurity controls, it’s essential to think about end-to-end security and work with a comprehensive approach to satisfy all requirements. This will maintain the continuity of your efforts, rather than just focusing on one control at a time.
Advantages of Proactive Cybersecurity
Improving cybersecurity controls may seem time-consuming and costly, but it’s far easier and safer than dealing with a security breach. A proactive approach will certainly cost you less in the long run, preventing the cascading effects of a security breach that never seem to end. It’s best to implement security practices, policies, and tools that help to detect and neutralize a breach before your environment is compromised. This will position your organization to minimize risk and achieve compliance expectations.
Here are seven best practices to help legal firms achieve required compliance:
Identify sensitive data you store and process: Law firms deal with tons of documents, and it’s impossible to ensure proper data protection before you determine which of those documents contain sensitive information. Sensitive information to look for:
- Payment and financial details
- Lawsuit information protected with non-disclosure agreements
- Health data
- Client and employee contact information
Implement cybersecurity policies: An incident response plan and insider threat protection program (to include ongoing security awareness training) are essential security policies for a law firm to develop. They describe procedures for managing and eliminating threats, helping you keep security measures at a high level, avoid confusion during a breach, and reduce breach reaction times, where time is of the essence.
Deploy an activity monitoring solution: A continuous user activity monitoring solution provides you with data on each action inside your protected perimeter. Such software deployed in a law firm monitors servers and endpoints, alerts security officers of suspicious user activity, records daily operations, and provides the means to review any security incident.
Encrypt stored sensitive data: If a hacker or malicious insider obtains encrypted sensitive information, it will be impossible to read and use. To access such files, a user or server has to request access rights from a content owner (also a user or server.) It’s best to encrypt data both at rest and in transit to ensure layered protection.
Control third-party actions: Attacking an organization through a third-party vendor is a common attack vector. Subcontractors usually have elevated access rights in the client’s environment, but they don’t always pay attention to security. To avoid such incidents, check a vendor’s compliance with cybersecurity standards and enforce access management and activity monitoring.
Manage access granularly: The idea of several access levels to corporate data is well-established in the legal industry. With digital data protection, it works the same way: security officers manage employees’ access to sensitive information and carefully adjust access levels to the needs of each employee. Best practice tells us that the minimum level of access should be provided to accomplish assigned duties.
Prevent unauthorized apps from executing in ways that compromise data: This can be accomplished through Application Control, allowing you to impose application-specific security policies for your legal firm. You can allow, deny, or limit specific types of application traffic.
Your Best Line of CyberDefense
When it comes to cybersecurity, your best line of defense is one that is comprehensive, follows the NIST framework & addresses your security needs now & in the future. Rather than addressing cyber threats singularly, a largely reactive response, a holistic approach to data protection will ensure that your IT environment is receiving the maximum protection 24/7/365, always-on, always ready.
If you’re concerned that your IT environment has holes that hackers can weave their way into critical data, take a no-cost, online self-assessment gauge that will show you where your weaknesses are. Use this information to prioritize the most serious gaps & plan to address those first.
If you have questions about how to go about prioritizing security needs, we are here to answer your questions. If you don’t have a tested response & recovery plan in the event of an attack, we can help you develop plans that protect your environment in the event of a disaster. And of course, if you’ve been hit by a cyber-attack, we are available to assist you in incident response recovering or restoring your systems.
For more educational resources on cybersecurity in the legal industry, visit our educational resources page.

