Scalable solutions
That grow with you
Business is filled with constant change. Staying ahead of those changes when it comes to managing your IT environment is essential in achieving your business goals. With Snap Tech IT Solutions, you can meet the changing needs of your business and develop a scalable strategy that grows with you. Expertise when and where you need it.
CyberDefense Solutions
Snap Tech IT CyberDefense has built security services around every aspect of the NIST CSF, providing the top-tier security you need to protect your business from sophisticated cyber-attacks. Explore CyberDefense Services by clicking on each section to learn more.
Plans that fit your needs
Whether you need Supplemental IT Management Solutions to support your existing IT infrastructure or Fully Managed IT Services, we have plans designed to solve your specific IT challenges.
You don’t have an IT department and need a Partner to manage your IT environment from end-to-end.
You have an IT Department managing your environment, but you could use an expert for projects and increasing workloads.
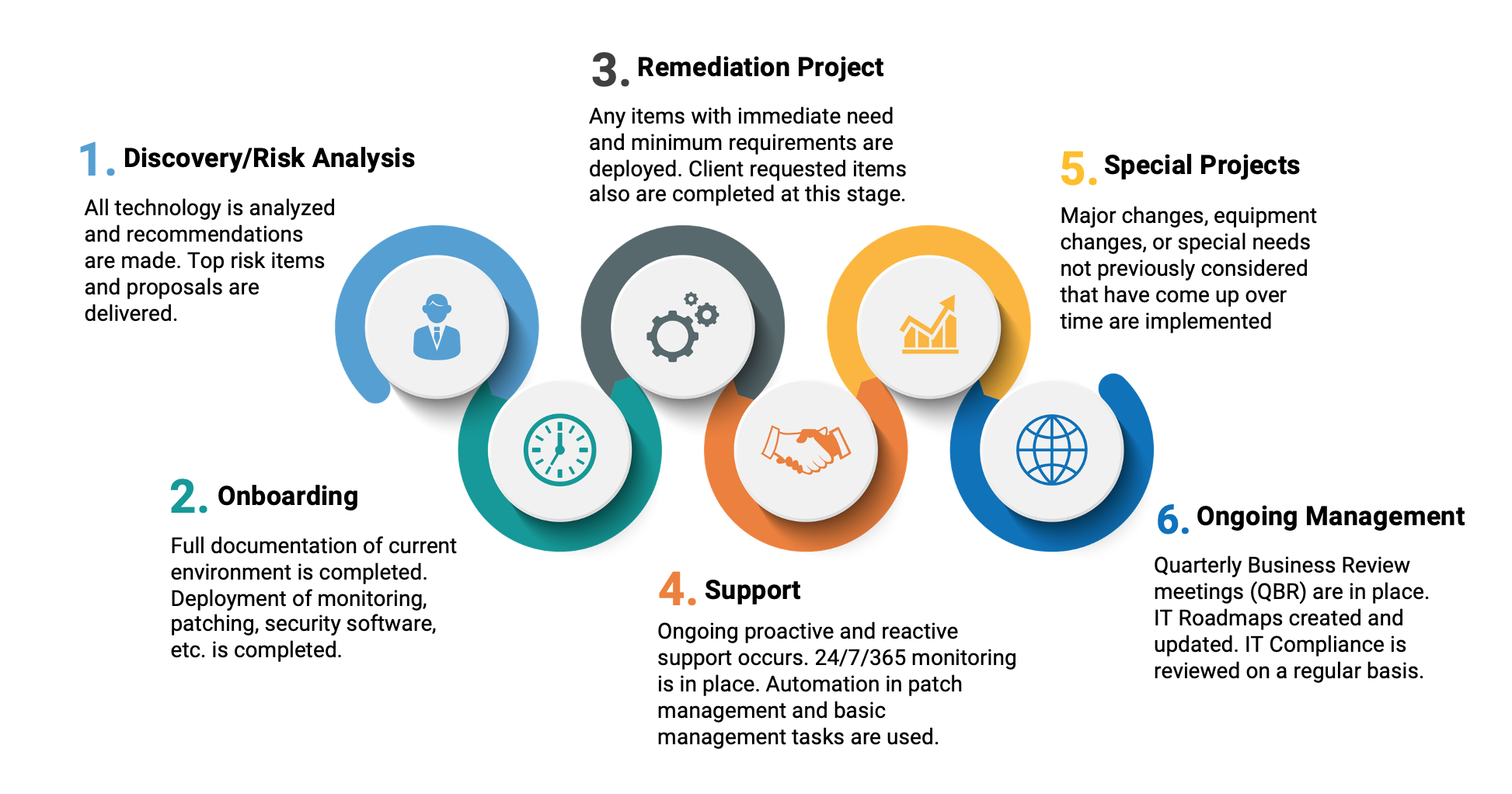
Proven Process
Straightforward, comprehensive & tailored to your business needs. A 360-degree proven process from risk analysis to Quarterly Business Reviews to maintain IT compliance. Manage. Secure. Grow.

On Demand Webinar
In this webinar, experts from Snap Tech IT and Datto discuss recent IDG research that explores IT decision-makers’ perspectives on cybersecurity. It’s estimated that hackers attack every 39 seconds, exposing critical business data that can lead to catastrophic financial and operational damages. Watch the webinar & learn how manage, detect, and respond to attacks.
Cloud Solutions
Supporting Managed and Co-Managed Services, our Cloud Solutions enable you to procure, manage, secure and back up a broad range of on-demand solutions.
- Cloud Applications: Office 365, Office 365 backup, dual factor authentication, email protection, encryption and archiving, secure cloud file solution, mobile device management (MDM), single-sign-on, system encryption
- Cloud Infrastructure: Microsoft™ Azure Cloud Servers, Virtual Desktops (VDI), Server & Desktop Backups, EndPoint Security
Professional Services
Maximize efficiency and manage key components of your IT environment with your dedicated project manager. Ensure projects and promises are always delivered on time, on budget and with the highest level of transparency.
- Cloud and Office 365 Migrations
- Network, Firewall, Laptop & PC Refreshes
- VoIP Phone Systems & Video Conferencing
Hungry for more
Explore our Resource Center and enrich your mind
- Blog
AI Cage Match: Google Gemini VS Microsoft Copilot

- Case Study
Case Study – TerraCorp

- Blog