Why the Department of Defense (DoD) created the cybersecurity maturity model certification (CMMC):
DoD contractors are now aware of the cybersecurity mandates that have been spreading into all areas of the defense industry and related government entities. In 2015 the DoD published the Defense Acquisition Federal Regulation Supplement known as DFARS. DFARS mandates the private DoD contractors adopt cybersecurity standard which follow the NIST SP 800-171 cybersecurity framework. This is all a government effort to protect the U.S. defense supply chain.
Since the DFARS mandate was released, contractors (including prime contractors and their subcontractors) have been trying to understand and implement these standards.
Previously the DoD has incentivized compliance by making it a competitive advantage in the contract awards process. Given the lack of punitive measures, many contractors have chosen not to implement the new standards or they are partially implementing convenient portions.
To further the problem, organizations have been self-attesting as to their compliance and there are documented cases where contractors have overstated their cybersecurity practices.
Due to the slow adoption of the standards, the DoD has released the CMMC to ensure the standards are being properly assessed and are adequate for their requirements.
The CMMC standard:
As of January 2020, the CMMC guidelines will be finalized. The guidelines specifically follow the DFARS requirement and map out the cybersecurity controls standards as documented in the NIST 800-171 framework. It also incorporates and uses controls found in several other cybersecurity and IT best practice frameworks such as NIST 800-53 and ISO 27001, among others.
The model is based on a measurement of all the controls and a maturity rating for each. The ratings range from the lowest maturity level of 1 to the highest of 5. Going forward it is expected that RFP will have stated CMMC maturity level requirements. Meaning, an RFP can only be answered by contractors that meet specific levels of maturity.
The CMMC will review and combine various cybersecurity standards and best practices and map these controls and processes across several maturity levels that range from basic cyber hygiene to advanced.
Here’s what we currently know about the CMMC levels and their respective requirements:
- Level 1 – “Basic Cyber Hygiene” – In order to pass an audit for this level, the DoD contractor will need to implement 17 controls of NIST 800-171 rev1.
- Level 2 – “Intermediate Cyber Hygiene” – In order to pass an audit for this level, the DoD contractor will need to implement another 48 controls of NIST 800-171 rev1 plus 7 new “Other” controls.
- Level 3 – “Good Cyber Hygiene” – In order to pass an audit for this level, the DoD contractor will need to implement the final 45 controls of NIST 800-171 rev1 plus 14 new “Other” controls.
- Level 4 – “Proactive” – In order to pass an audit for this level, the DoD contractor will need to implement 13 controls of NIST 800-171 RevB plus 13 new “Other” controls
- Level 5 – “Advanced / Progressive” – In order to pass an audit for this level, the DoD new “Other” controls.
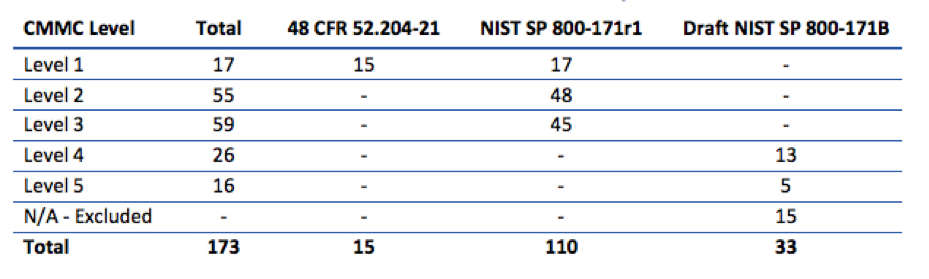
Note: This information is based on Version 0.7 of the CMMC model. The number of controls per level could change in future revisions of the CMMC model. We will update this document as official updates are released.
No More Self Attestation:
The DoD will deploy certified 3rd party assessor organizations to conduct audits on the DoD contractors. From this audit an organization will be given a level of maturity rating which each level accomplished must have 100% adherence.
Your Organization’s Readiness Assessment for CCMC:
In order to determine your organizations readiness for this certification you will need to review all the domain of cybersecurity and the related controls each domain has attached to it. The list of domains almost identically matches the NIST SP 800-171 rev 1 domains exactly. Here are the domains:
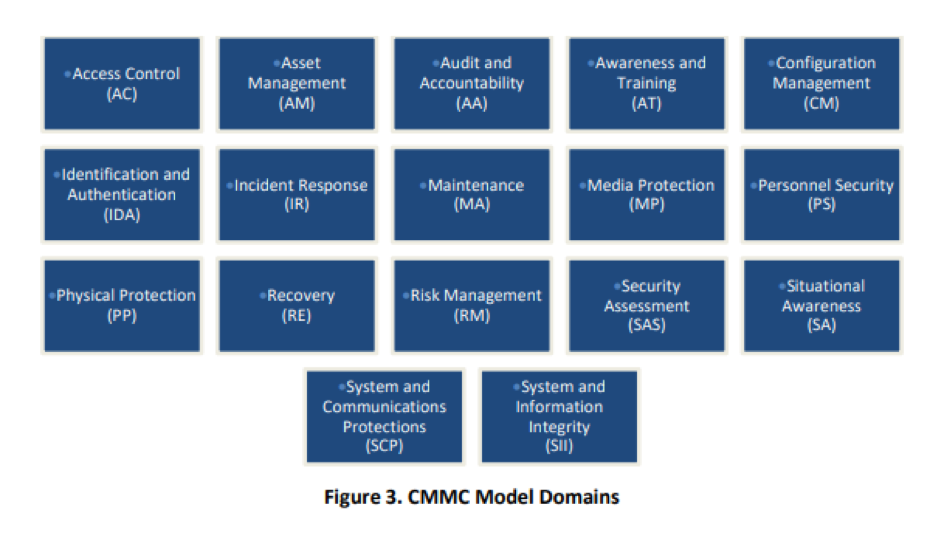
Where the CMMC differs from the NIST and other guidelines below is that is specifics a set of capabilities and process maturity levels for them. Here are the current list of capabilities and the process maturity level matrix the current version of the CMMC has published:
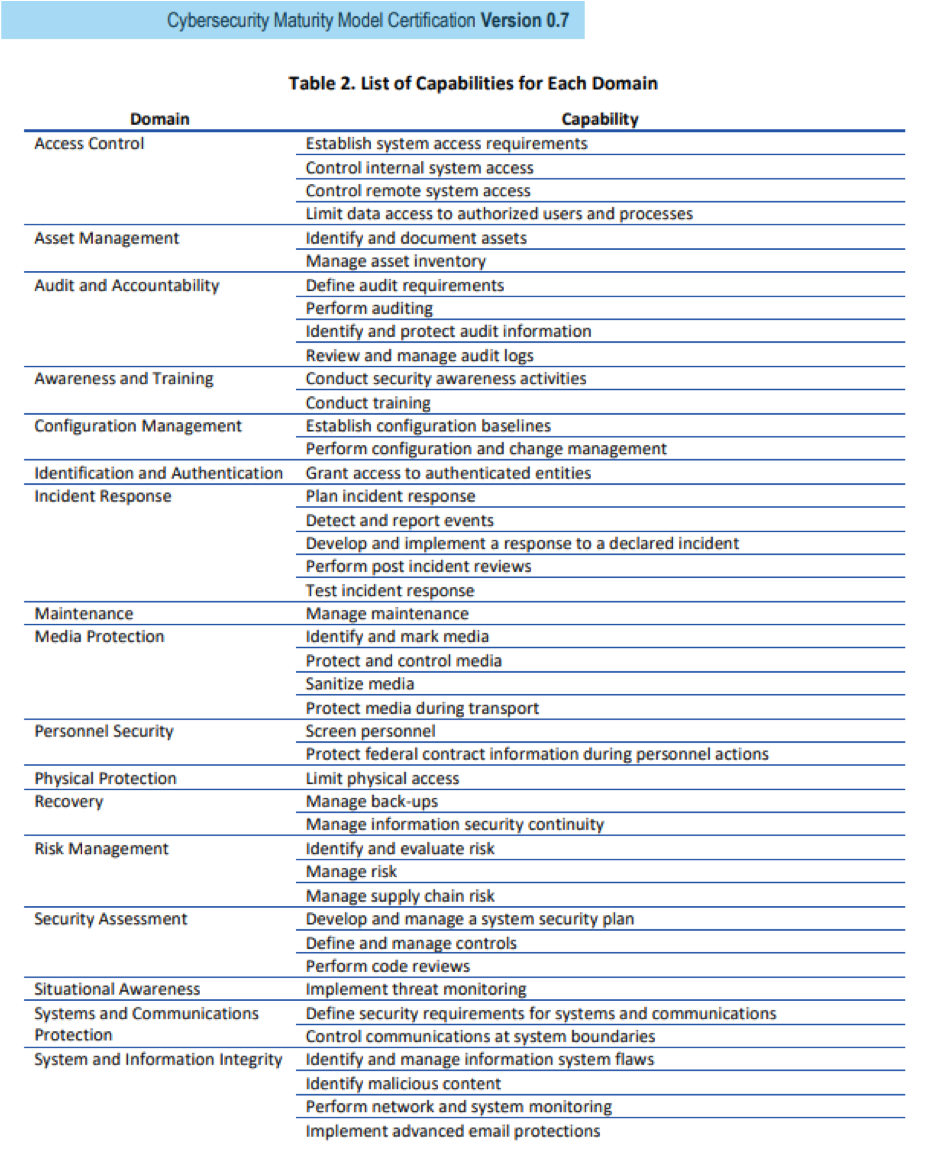
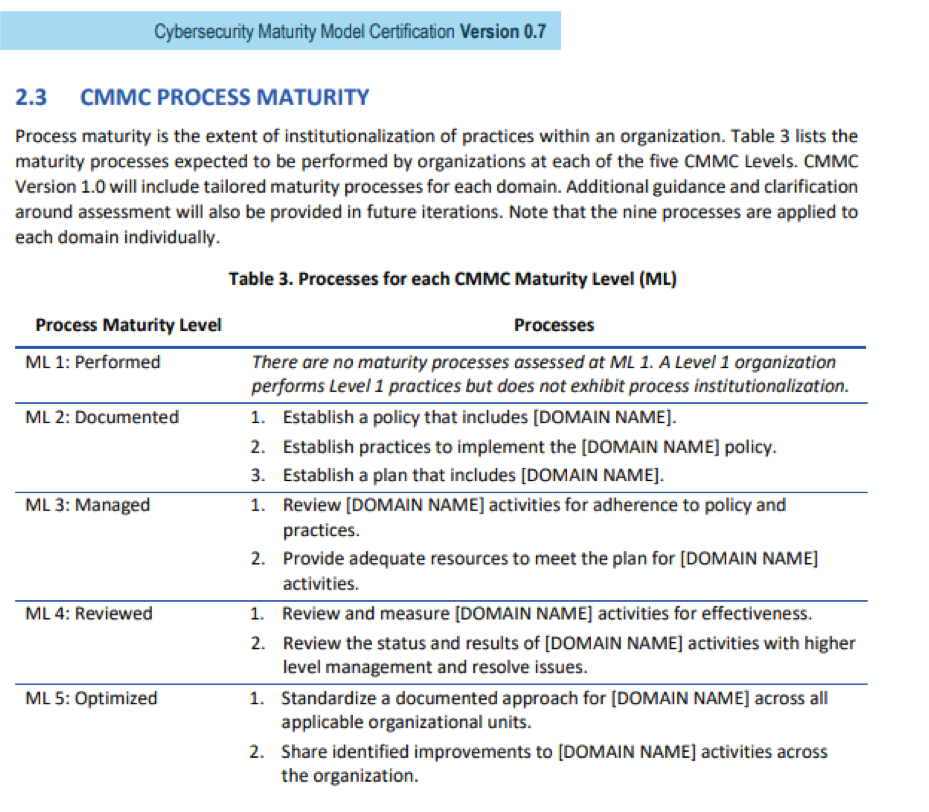
They key elements for moving forward are this:
- You need get a risk assessment done on your organization by an independent 3rd party to know where you really stand on the CMMC standard.
- You need to figure out what maturity level you want to set as your target. It is expected that most are going to need to get to the level 3 mark to be able to win the bids they are wanting.
- You need to identify the capabilities and controls that need to be implemented to reach your target maturity level.
- You need to identify the needed processes, policies, and plans required to meet the maturity level goal.
- You need an action plan that sets your IT budget and timing to reach your target maturity level.

From what we have seen in the DoD subcontractor space, there are a lot of organizations that are going to need to dramatically change their existing practices in the area of IT. Most are well-meaning manufacturers that have been handling their IT the same way for years. That lack of adapting has built a technical debt that they must know find their way out of in order to maintain their existing business and, just as importantly, they will need to get onboard with this in order to participate in the enormous amount of new spending the DoD and other federal agencies are expected to do. To grow your federal business, you will need to have good scores on your CMMC.
This is a very achievable standard, but you need to make sure you have the expertise, the budget, the management and the high level of direct involvement, to ensure the success of it. This is not a standard that can be achieved by your IT team alone. It will require involvement and education for all levels of your organization, and it will need to be driven from your entire management team.