If your company is like most, improving cybersecurity is at the top of everyone’s agenda these days; however, it is an enormous task, and many people don’t know where to start. I suggest that we start with a proven framework. So, today we are going to look at the National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) and how it can help your company improve its cybersecurity and better protect against cyber-attacks.
Where did this framework come from? I could write an entire article about where the framework originated and how it was developed. The short answer is that it was developed by the National Institute of Standards and Technology (NIST) after several executive orders that started in 2014 with the current version, 1.1, being released in 2018. The important thing to understand is that this framework was not developed overnight, and thousands of hours of research and input from industry experts, academia and the government went into developing the framework.
“Cybersecurity is critical for national and economic security,” commented Secretary of Commerce Wilbur Ross. “The voluntary NIST Cybersecurity Framework should be every company’s first line of defense. Adopting version 1.1 is a must do for all CEO’s.”
Now that we know a little history about the NIST Cybersecurity framework, let’s dive in and learn about its components and how we can use the cybersecurity framework to improve the security of our businesses.
NIST CSF Components
The NIST CSF is broken down into 3 main components: Framework Core, Framework Implementation Tiers, and Framework Profiles.
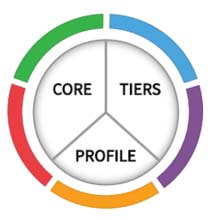
Framework Core
The Framework Core defines a set of desired outcomes for your organization to achieve as a means of improving cybersecurity. The Framework Core is further broken down into 3 parts: Functions, Categories, and Sub-Categories.
Functions
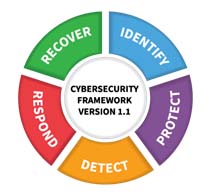
There are 5 Functions in the NIST CSF. These functions provide the high- level cybersecurity tasks that your organization needs to address and improve your cybersecurity. These Functions are: Identify, Detect, Protect, Respond, and Recover.
Categories
Each Function is further defined and broken down into Categories. For example, the Identify Function has the following Categories: Asset Management, Business Environment, Governance, Risk Assessment, Risk Management Strategy, Supply Chain Risk Management.
Sub-Categories
Sub-Categories are where the rubber meets the road, and these define the granular details of the desired outcomes. Some of these Sub-Categories are straight forward and easy to understand the desired outcome. For example, ID.AM-1, which is in the Identify (ID) Function, Asset Management (AM) Category, and the Sub-Category: Physical devices and systems within the organization are inventoried. I think we all have a pretty good idea of what the desired outcome of this Sub-Category is; however, some of the Sub-Categories can be a little tricky to understand. To help with this, the NIST CSF includes Informative References.
Informative References
The Informative References are part of the Framework Core, and they provide the technical references or security controls for implementing the practices to achieve desired outcomes from the Sub-Categories. To continue our example above, if we had questions about how to accomplish this desired outcome, we could use the Informative References for this Sub-Category, and look up CIS Control 1 for more information about how to attain the goal in our environment.
Implementation Tiers
Let me first start by saying that the Implementation Tiers are not intended to represent an organization’s maturity as it relates the its cybersecurity practice and risk management. However, I have found that the best way to describe the Tiers is to explain that they are essentially maturity levels. There are 4 Implementation Tiers defined in the NIST CSF:
- Tier 1 – Partial Implementation – Organizations at Tier 1 have an ad-hoc, non-formalized, and reactive approach to cybersecurity and risk management.
- Tier 2 – Risk Informed – Organizations at Tier 2 are aware of cybersecurity risk, but still may not have an organizational-wide policy for security risk management. They may also have plans and resources to protect the organization, but are still not proactive in their approach.
- Tier 3 – Repeatable – Organizations at Tier 3 have a Risk Management plan that is followed and is defined by a security policy. Routinely review and update their cybersecurity practices based on the changes in the business requirements.
- Tier 4 – Adaptive – Organizations at Tier 4 will constantly review, respond and adapt their cybersecurity policies based on lessons learned, predictive indicators, best practices and internal security events that occur in their company. These organizations will also have a strong company culture around cybersecurity risk management, and their senior executives will treat cyber risk the same as financial risk.
Framework Profiles
Framework Profiles is the align of the Functions, Categories and Subcategories to the business requirements and risk tolerance. An organization should start by defining their Current Profile, which indicates the cybersecurity outcomes that they are currently achieving. Next, develop a Target Profile that defines the outcomes that need to be satisfied for the organization’s risk management goals. Comparing these two profiles will reveal the gaps in your cybersecurity that need to be addressed in an Action Plan.
By: Shawn Brown, COO, Snap Tech IT
Next Time
In our next blog, we are going to dive into: How to Use a Risk Assessment to Improve Your Company’s Cybersecurity.
Cybersecurity Assessment
Identify the risk to your IT environment by scheduling time with an IT consultant.