
Comprehensive Risk Assessment Process
Understand your Vulnerabilities Assessments of security risk require a methodical approach that begins with knowing your critical security gaps. One of the best ways to

Understand your Vulnerabilities Assessments of security risk require a methodical approach that begins with knowing your critical security gaps. One of the best ways to

The American Bar Association’s 2021 Legal Technology Survey Report shines a light on security gaps among small to medium-sized firms that expose vulnerabilities, leading to sensitive data breaches, loss of billable hours & reputational damages. Explore key findings & learn simple tips to neutralize your risk.
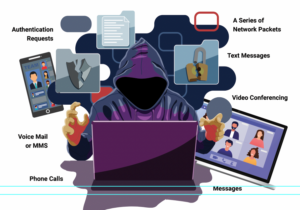
The cyber-attacks threat continues to intensify for businesses all across the United States. A method known as Zero-Click hacking is becoming increasingly prevalent, often pushed by governments onto individuals and activist groups. This is key, since phones are often the method of entry, which, in many cases, is tied to system networks. Learn more about how these attacks work and what you can do to minimize your risk exposure.

Financial Compliance-More than most types of business, financial management firms carry a heavy burden to avoid cybersecurity risk and protect their client’s sensitive information. This is because cyber criminals mark them as a high-value target, which in turn leads to the needs for IT compliance.

A Tactical Guide to Social Engineering- 70-90% of all malicious breaches are due to social engineering & phishing attacks. Hackers love to prey on human weaknesses like Sympathy, Fear, Trust, Laziness, Ignorance, Greed, and Ego.

Phishing is the first delivery method for other types of malicious software. A phishing attack isn’t just targeted at
gaining information. but they can also be used to distribute malicious programs, such as ransomware.

According to Gartner— 50% of organizations will be using Managed Detection and Response services for threat monitoring, detection, and response functions that offer threat containment capabilities.

You’ve heard the benefits of transitioning to the cloud. It’s cost-effective, easier to use, more flexibility, and the list goes on. But, many businesses wrestle with how they will secure the data in the cloud. And for good reason. Give your data the protection it needs with Cloud Solutions from Snap Tech IT.

In a post-pandemic world, businesses are understanding the true value behind IT expertise & management of cybersecurity.
18 Bartol Street Suite 183
San Francisco, CA 94133
415-970-0100