CMMC Compliance: Essential for Data Security

Byline: Ted Hulsy, CRO, Snap Tech IT
If your business handles defense contracts, you have undoubtedly heard of CMMC (Cybersecurity Maturity Model Certification). In the world of data protection and cybersecurity, ensuring compliance with best practices has never been more essential – especially when it comes to government contracts.
So, what is CMMC? And how can you make sure your business complies? This blog post will uncover the answers to these questions so that you can ensure your business operates securely and meets all necessary requirements. Read on to find out everything about CMMC compliance.
Understanding CMMC Compliance
CMMC is a unified standard created to ensure that DoD contractors have adequate cybersecurity defenses in place to protect sensitive information. The objective of CMMC compliance is to enhance the cybersecurity posture of organizations in the defense supply chain and safeguard the confidentiality of government data. Non-compliance with CMMC can result in the loss of contracts and significant reputational damage. Therefore, it’s critical for organizations that interact with the DoD to become CMMC compliant and maintain an elevated level of cybersecurity maturity.
What is CMMC 2.0?
The implementation of CMMC 1.0 was met with a compliance bottleneck due to the overwhelming number of firms requiring third-party assessments. Unfortunately, the total number of available CMMC Third-Party Assessor Organizations (C3PO) was not growing rapidly enough to meet demand. As a result, the Department of Defense (DoD) acted swiftly to address these concerns with the release of CMMC 2.0.
The new framework simplifies the compliance process and reduces its burden, which is especially beneficial for the tens of thousands of smaller companies that comprise the bulk of the defense industrial base (DIB). The DoD recognizes that cybersecurity maturity and investment can be achieved just as effectively through a tiered approach, with the vast majority of firms self-attesting to compliance. CMMC 2.0 addresses the bottleneck of third-party assessors and acknowledges the vast differences in risk management between smaller manufacturers and large, sophisticated prime contractors.
With CMMC 2.0, companies have more flexibility and can make real, concrete investments in cybersecurity without necessarily engaging third-party assessors or auditors. These changes give companies greater control over their compliance efforts.
Let’s examine the most significant changes in the new CMMC framework.
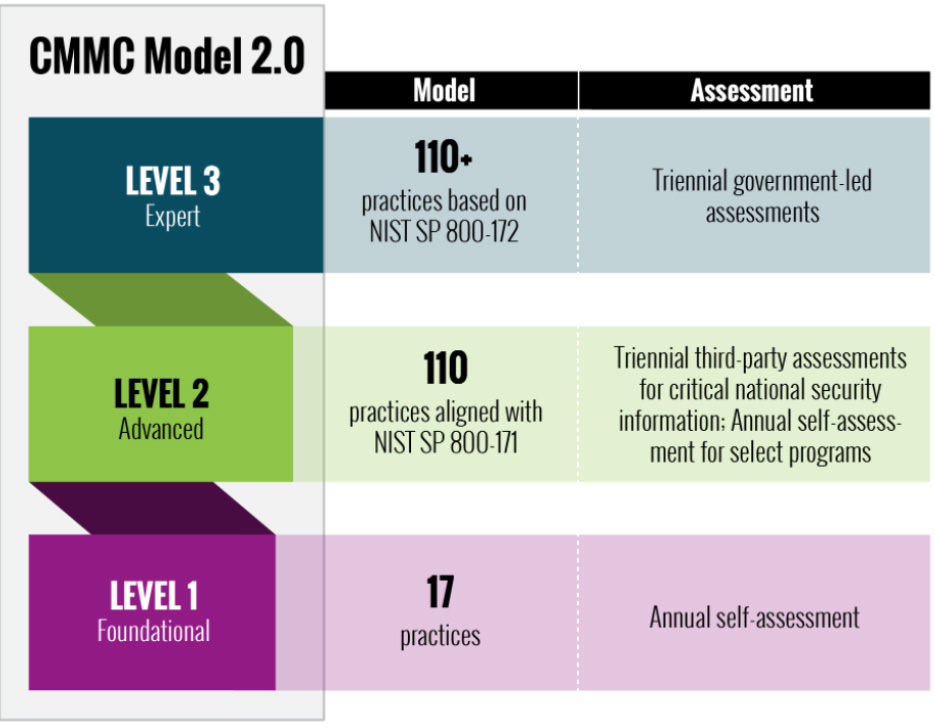
What are the CMMC 2.0 levels?
- Level 1: This level of compliance is mandatory for all federal contractors in possession of Federal Contract Information (FCI).
- Level 2: This level of compliance is required for all federal contractors handling:
- Controlled Unclassified Information (CUI) / Controlled Defense Information
- Controlled Technical Information (CTI)
- ITAR or export-controlled data
- Level 3: This level applies to companies that handle CUI for DoD programs with the highest priorty.
What are the CMMC 2.0 level requirements?
- Level 1: the Department of Defense has classified a set of cybersecurity practices as “Basic” for FCI handling. To meet the Level 1 requirement, contractors must implement 17 basic cybersecurity practices and self-attest to their successful implementation.
- Level 2: 110 practices, including those mandated by NIST SP 800-171, and subject to third-party assessments for “critical” national security information. It is important to note that Defense Federal Acquisition Regulation Supplement (DFARS) already mandated compliance to NIST 800-171 controls and was already the law of the land for federal sub-contractors before the advent of CMMC.
- The new CMMC 2.0 framework introduces a “bifurcated” approach for Level 2 organizations. For companies participating in “critical” programs or “prioritized acquisitions,” companies must undergo a third-party assessment every three years and conduct annual self-assessments. Subcontractors can rely on their prime contractors to determine if their supply agreements fall under prioritized acquisitions.
- For all other contractors at Level 2, the contractor should perform an annual self-assessment or self-attestation. In our view, the vast majority of defense subcontractors will fall into this category.
- Level 3: Requires adherence to NIST 800-171 and certain elements of the NIST 800-172 standard. Compliance is evaluated and audited through government-led assessments. The additional requirements and steps for Level 3 are beyond the scope of this blog.
Steps to Achieve CMMC Compliance
- Work with a third-party Registered Provider Organization (RPO) to conduct a CMMC Readiness Assessment
- Document System Security Plan (SSP), Plan of Action and Milestones (POAM), and determine Supplier Performance Risk System score (“SPRS score”)
a. SSP: A system security plan (SSP) is a document that describes the security controls that are in place to protect an information system. The SSP is a critical part of an organization’s overall information security program.
b. POAM: A document that identifies tasks needing to be accomplished. It details resources required to accomplish the elements of the plan, any milestones in meeting the tasks and scheduled completion dates for the milestones. POAMs are often used in the context of cybersecurity, where they are used to document the steps that will be taken to address security vulnerabilities. POAMs can also be used in other contexts, such as project management or business process improvement.
c. SPRS score: or Summary Level Score, is a measure of a contractor’s compliance with the NIST SP 800-171 cybersecurity framework. The SPRS score is calculated by the Supplier Performance Risk System (SPRS), a database maintained by the Department of Defense (DoD). The SPRS score is used by the DoD to assess the security risk of contractors who manage sensitive information.
3. Leverage a governance, risk, and compliance (GRC) tool:
- A GRC tool is a software application that helps organizations manage their governance, risk, and compliance (GRC) initiatives. GRC tools can be a valuable asset for organizations of all sizes. By using a GRC tool, organizations can improve their governance, risk, and compliance posture and reduce their risk of data breaches and other security incidents.
- GRC tools can help organizations to:
- Identify and assess risks: GRC tools can help organizations to identify and assess the risks that they face, both internally and externally.
- Develop and implement controls: GRC tools can help organizations to develop and implement controls to mitigate the risks that they have identified.
- Monitor and report on compliance: GRC tools can help organizations to monitor their compliance with regulations and industry standards.
4. Educate and train employees: GRC tools can help organizations to educate and train employees on compliance and risk management best practices.
5. Implement Necessary Security Controls and Practices, based on whether your organization is Level 1, Level 2, or Level 3.
For most organizations, the process of complying with all 110 controls in NIST 800-171 can take several months or even a few years to achieve, based on the current cybersecurity maturity of the organization.
6. For Level 2 organizations not involved in “critical programs,” prepare for self-attestation on CMMC compliance.
7. For Level 2 organizations involved in “critical programs,” prepare for third-party (C3PAO) or government-led assessments.
8. For Level 3 organizations, prepare for government-led assessments.
Benefits of CMMC Compliance
The benefits of Cybersecurity Maturity Model Certification (CMMC) are numerous, and they extend far beyond simply complying with government regulations. One of the most significant advantages of CMMC compliance is increased cybersecurity and risk mitigation. By establishing a solid set of security protocols and best practices, organizations can protect themselves from breaches, data loss, and other security threats.
Additionally, achieving CMMC certification can give companies a competitive advantage in government contracts, as more government entities are requiring contractors to be certified. Being CMMC compliant also helps demonstrate an organization’s trustworthiness to customers and partners, giving them peace of mind and ensuring long-term business relationships. Early adopters of the CMMC approach will build with key customers and likely win more than their fair share of business as the CMMC compliance process matures.
Finally, CMMC compliance ensures protection of sensitive information and intellectual property, safeguarding business interests and sensitive data. Overall, achieving CMMC certification can bring a wealth of benefits to manufacturers of all sizes.
Conclusion
CMMC compliance is crucial for any company dealing in information related to supplying the Department of Defense. To ensure the security of this sensitive data, businesses must obtain a certification that proves their ability to meet cybersecurity standards set by the government. Achieving these certifications can be an arduous process and likely require the assistance of knowledgeable professionals who are dedicated to helping companies achieve compliance.
Attaining CMMC compliance is worth it for companies as they protect not only their property, but also the safety and security of the US armed forces. Compliance is also an important way for companies to remain competitive and relevant in today’s world and highlights the seriousness with which businesses take cyber security.