Snap Tech IT Receives SOC 2 Type II Attestation

Snap Tech IT Receives SOC 2 Type II Attestation Independent Audit Verifies Snap Tech IT’s Internal Controls and Processes TEMPE, Ariz., February 21, 2022 – Snap Tech IT, a managed services & cybersecurity provider, today announced that it has completed its SOC 2 Type II audit, performed by KirkpatrickPrice. This attestation provides evidence that Snap […]
Financial Webinar: Striking a Balance

Join cybersecurity experts, Karl Bickmore, CEO, Snap Tech IT, & Shawn Brown, COO, Snap Tech IT for a 30-minute conversation on Striking a Balance Between Financial Compliance & Cybersecurity
7 Cybersecurity Practices for Legal Firms

7 Cybersecurity Practices for Legal Firms By: Karl Bickmore, COO, Snap Tech IT Handling sensitive data that attracts hackers and malicious insiders is part of everyday life in a law firm. The majority of security breaches lead to some form of reputational losses, remediation costs, and penalties. That’s why there are 7 cybersecurity best practices […]
Running Rampant: Exposing Cybersecurity Challenges Affecting the Banking Industry

Cybersecurity attacks are evolving, becoming more sophisticated, more frequent, and much more widespread, leading to elevated operational risks to banks and financial firms as a whole.
Does Your Financial Management Organization Meet IT Compliance Needs?

More than most types of business, financial management firms carry a heavy burden to avoid cybersecurity risk and protect their clients’ sensitive information. This is because cybercriminals mark them as a high-value target, which in turn leads to needs for IT compliance. Whenever I meet with owners and managers of financial firms to discuss their […]
Multi-Factor Authentication Lowdown
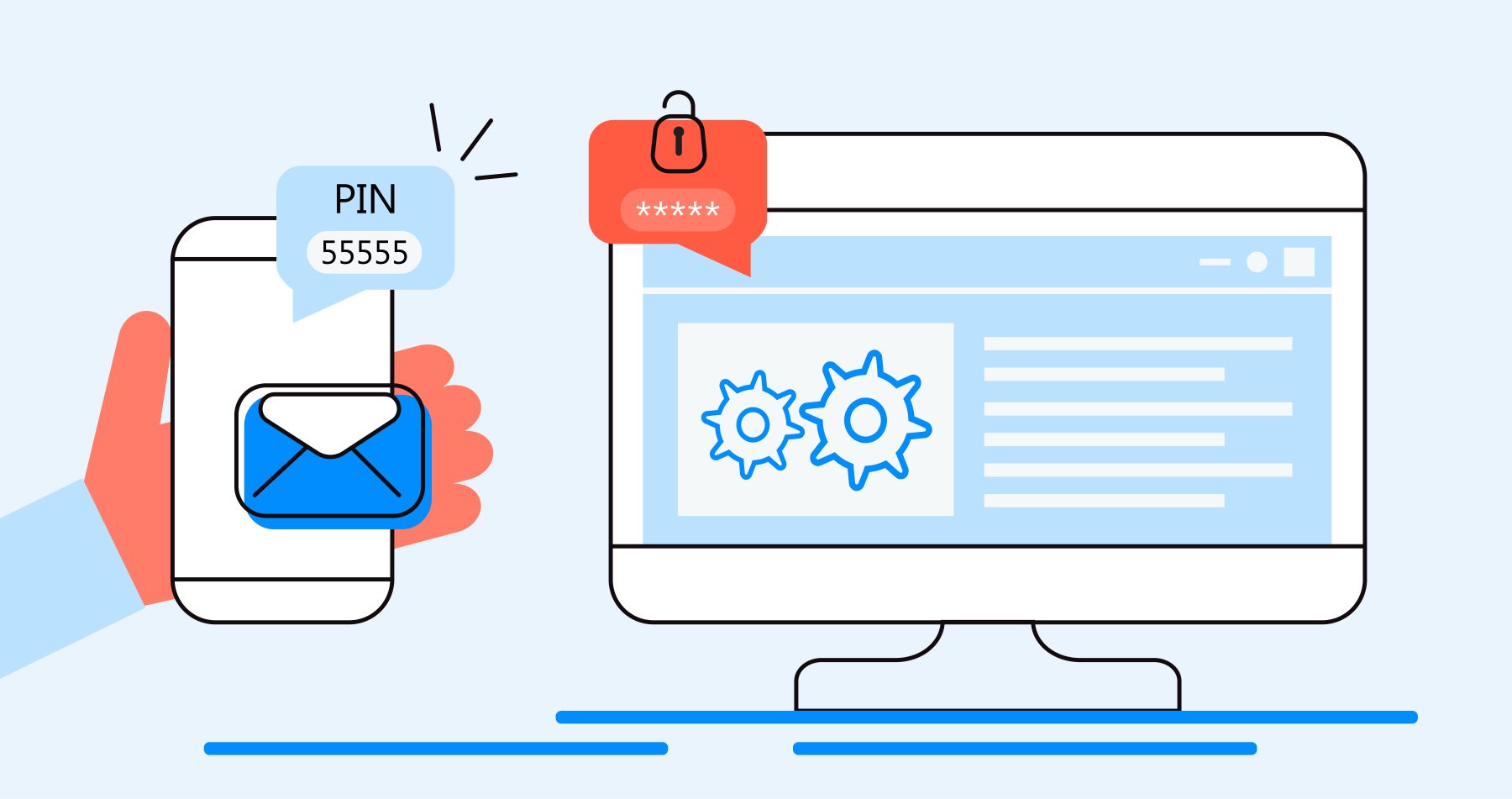
As businesses take necessary steps to shore up security in their environments, one of the most critical tools out there comes to mind as a must-have for anyone looking to keep the hackers out is multi-factor authentication. Authentication, in its simplest form, is the process of confirming that someone attempting to enter your environment is who they claim to be. Protecting your IT environment and sensitive data depends on knowing exactly who is trying to gain access.
Cybersecurity Self-Assessment

A self-assessment is the first step to understanding your IT environment, your processes, and what gaps you have in your security program.
A Less Expensive and Easier to Use Legal Research Tool

By: Karl Bickmore, CEO, Snap Tech IT Whenever I come across a useful new tool on the market that I think might benefit our customers, I’m always eager to share it. And what better way to get the information to the most people possible than blogging about it? I recently had one of those moments, when […]
Fundamentals of Firewalls at a Glance

Web Security at a Glance: Firewall Fundamentals by Karl Bickmore When was the last time you got into your car without fastening your seatbelt? That was probably a long time ago, depending on your age, before it became widespread knowledge that seat belts save lives. Having a firewall to protect against harmful web attacks is the […]