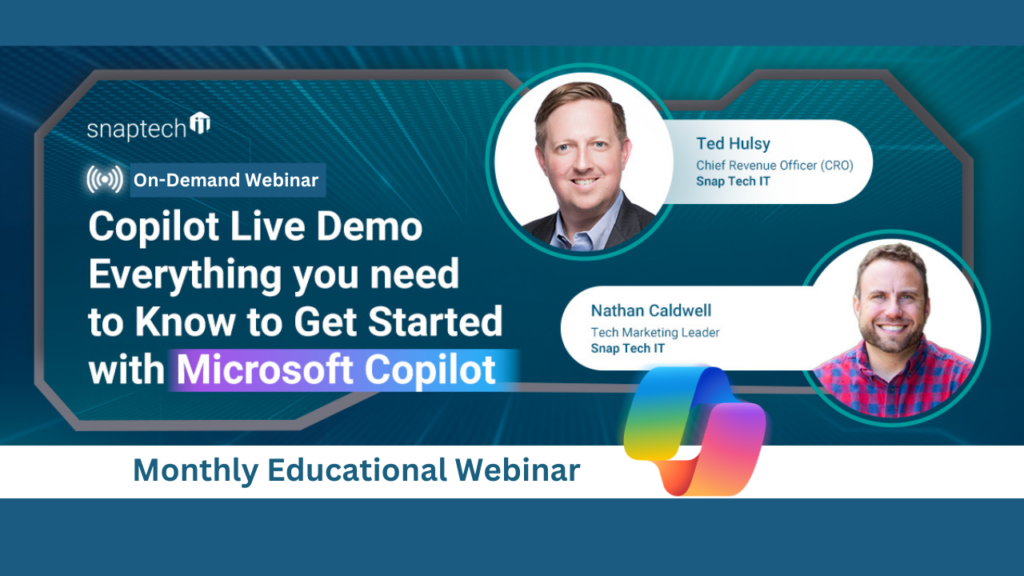
Microsoft Copilot Demo: Everything You Need To Know About Copilot – Webinar Recording
A culture of cybersecurity doesn’t just happen. Learn how to build a culture of cybersecurity in your organization by watching our on-demand webinar.
Cybersecurity Awareness Month: How to Build a Culture of Cybersecurity – Webinar Recording

A culture of cybersecurity doesn’t just happen. Learn how to build a culture of cybersecurity in your organization by watching our on-demand webinar.
How Defense In Depth Will Save Your Business From Cybersecurity Breaches and Data Loss – Webinar Recording

Explore strategic ways to get more out of Microsoft Teams. Learn how to organize your Teams experience to improve communication across your company helping you to become a Microsoft Teams power user.
Watch this on-demand webinar to learn the Top 10 Tips to Get the Most Out of Microsoft Teams.
Snap Tech IT’s 2024 Outlook
Join us we look forward to the new year in “Snap Tech IT’s 2024 IT Outlook.” The IT landscape is poised for critical changes, impacting businesses of all sizes and across industries. This webinar is your opportunity to gain valuable insights into the technology trends and strategies that will shape the IT landscape in the coming year.
Ask a Hacker How New AI Tools are Making Hackers Even More Dangerous

In today’s digital landscape, the evolution of artificial intelligence (AI) and machine learning (ML) technologies has not only revolutionized businesses but has also empowered cybercriminals with advanced tools and techniques. Join us for an intriguing webinar, “Ask a Hacker,” where we delve into the fascinating world of AI-driven hacking and discuss how these emerging technologies are enabling cybercriminals to become even more dangerous.
Dark Web Monitoring: How It Works

As we enter the digital age, the significance of cybersecurity has never been clearer. As technology becomes ingrained in our everyday existence, the threats to our digital world continue to evolve. In 2023, organizations will be confronted with a new set of cybersecurity challenges that require immediate attention and strategic solutions.
Learn how dark web monitoring works and why it’s crucial for safeguarding your business against credential theft and data breaches. Explore the layers of the dark web, its potential threats, and how monitoring services can help identify and mitigate risks effectively. Discover the business benefits and find out how Snap Tech IT can enhance your cybersecurity strategy.
Seven Reasons Microsoft 365 Business Premium Is the Right Choice for Businesses

As we enter the digital age, the significance of cybersecurity has never been clearer. As technology becomes ingrained in our everyday existence, the threats to our digital world continue to evolve. In 2023, organizations will be confronted with a new set of cybersecurity challenges that require immediate attention and strategic solutions.
This blog will summarize the discussion from our recent webinar and investigate the top five cybersecurity challenges of 2023, shedding light on the changing landscape and the measures organizations must implement to protect their digital assets.
NIST Cybersecurity Framework

As we enter the digital age, the significance of cybersecurity has never been clearer. As technology becomes ingrained in our everyday existence, the threats to our digital world continue to evolve. In 2023, organizations will be confronted with a new set of cybersecurity challenges that require immediate attention and strategic solutions.
This blog will summarize the discussion from our recent webinar and investigate the top five cybersecurity challenges of 2023, shedding light on the changing landscape and the measures organizations must implement to protect their digital assets.
Top Five Cybersecurity Challenges of 2023

As we enter the digital age, the significance of cybersecurity has never been clearer. As technology becomes ingrained in our everyday existence, the threats to our digital world continue to evolve. In 2023, organizations will be confronted with a new set of cybersecurity challenges that require immediate attention and strategic solutions.
This blog will summarize the discussion from our recent webinar and investigate the top five cybersecurity challenges of 2023, shedding light on the changing landscape and the measures organizations must implement to protect their digital assets.